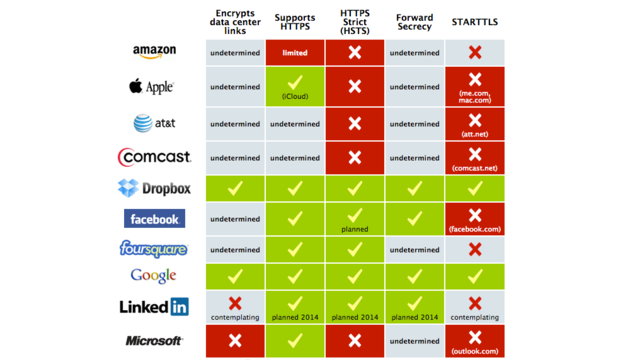
Google vs. Microsoft: Guess Which Company Isn’t Encrypting Your Data?
November 20, 2013
2 minute read

In a recent survey released by the Electronic Frontier Foundation of the top technology companies, Microsoft fails to comply with a number of data encryption and security recommendations while Google excels on all fronts.
To ensure data security, the EFF recommends technology companies follow protocols in five areas:
1. Encrypt Websites with Hypertext Transfer Protocol Secure (HTTPS)
If HTTPs is implemented, communications between a user’s computer and the given website are encrypted.
Google and Microsoft are both compliant.
2. Enable HTTP Strict Transport Security (HSTS)
However, to ensure the communication remains secure, companies should enabled HTTP Strict Transport Security or HSTS. HSTS uses secure communications to prevent certain attacks if a network pretends that the site visited has asked to communicate insecurely.
Microsoft is non-compliant.
3. Encrypt Data Center Links
This protocol asks companies to encrypt communications between a company’s own cloud servers and their data centers. This precaution ensures data is protected in the case that an attacker has access to physical data links or has compromised network equipment.
Microsoft is non-compliant.
4. Implement STARTTLS for email transfer
STARTTLS is an opportunistic encryption system, which encrypts communications between email servers that use the Simple Mail Transfer Protocol (SMTP) standard. If users operating on different email servers (ie. Gmail and Outlook.com) email one another, data must travel over the internet. If both servers understand STARTTLS the communication is encrypted in transit. However, if only one of the two complies with STARTTLS, the data is vulnerable to surveillance.
Microsoft’s Outlook.com is non-compliant – more reason than ever to make sure everyone in your company has a standard email address.
5. Use Forward Secrecy for Encryption Keys
Forward secrecy is designed to protect communications previously encrypted regardless of whether or not one of the service providers’ keys is later compromised. If a provider fails to implement Forward Secrecy, an attacker who gains access to a service provider’s secret key can use that key to read previously encrypted communications.
Microsoft’s compliance is undetermined.
For more on the findings, visit Gizmodo here.